Shiro authentication for Apache Zeppelin
Overview
Apache Shiro is a powerful and easy-to-use Java security framework that performs authentication, authorization, cryptography, and session management. In this documentation, we will explain step by step how Shiro works for Zeppelin notebook authentication.
When you connect to Apache Zeppelin, you will be asked to enter your credentials. Once you logged in, then you have access to all notes including other user's notes.
Security Setup
You can setup Zeppelin notebook authentication in some simple steps.
1. Secure the HTTP channel
To secure the HTTP channel, you have to change both anon and authc settings in conf/shiro.ini. In here, anon means "the access is anonymous" and authc means "formed auth security".
The default status of them is
/** = anon
#/** = authc
Deactivate the line "/** = anon" and activate the line "/** = authc" in conf/shiro.ini file.
#/** = anon
/** = authc
For the further information about shiro.ini file format, please refer to Shiro Configuration.
2. Secure the Websocket channel
Set to property zeppelin.anonymous.allowed to false in conf/zeppelin-site.xml. If you don't have this file yet, just copy conf/zeppelin-site.xml.template to conf/zeppelin-site.xml.
3. Start Zeppelin
bin/zeppelin-daemon.sh start (or restart)
Then you can browse Zeppelin at http://localhost:8080.
4. Login
Finally, you can login using one of the below username/password combinations.
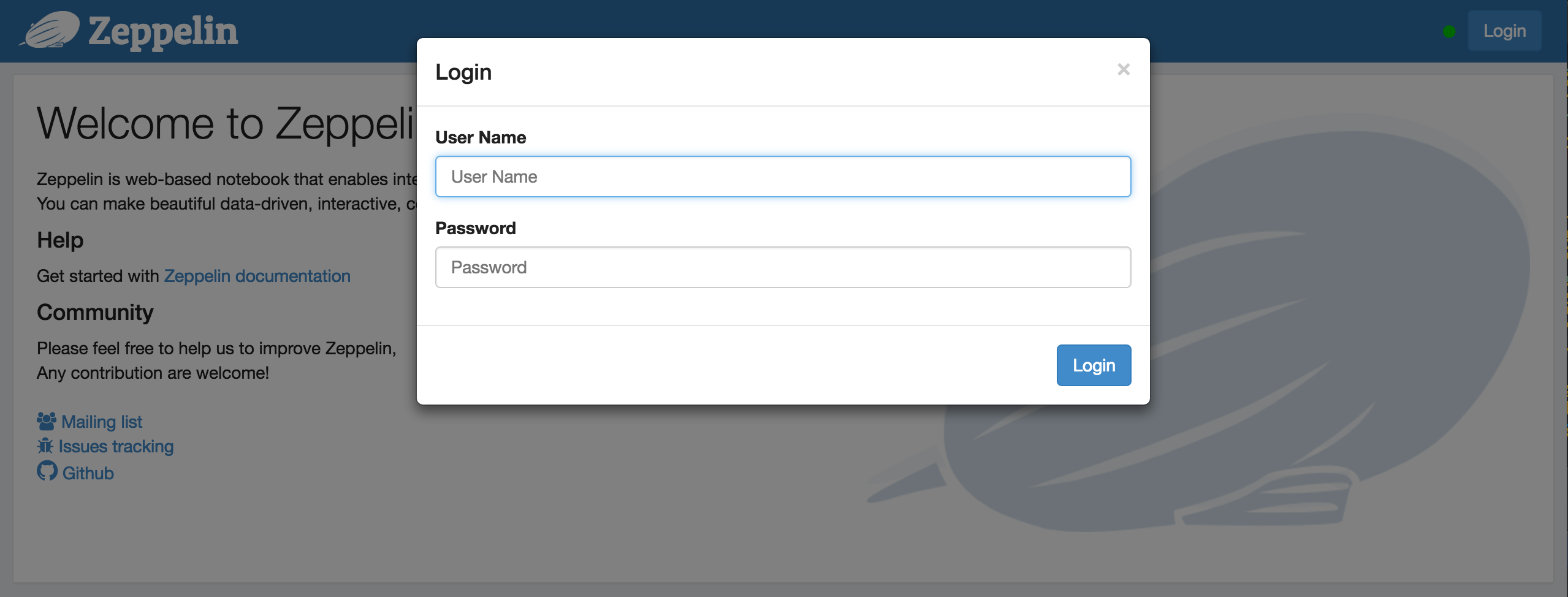
admin = password1
user1 = password2
user2 = password3
5. Groups and permissions (optional)
In case you want to leverage user groups and permissions, use one of the following configuration for LDAP or AD under [main] segment in shiro.ini
activeDirectoryRealm = org.apache.zeppelin.server.ActiveDirectoryGroupRealm
activeDirectoryRealm.systemUsername = userNameA
activeDirectoryRealm.systemPassword = passwordA
activeDirectoryRealm.searchBase = CN=Users,DC=SOME_GROUP,DC=COMPANY,DC=COM
activeDirectoryRealm.url = ldap://ldap.test.com:389
activeDirectoryRealm.groupRolesMap = "CN=aGroupName,OU=groups,DC=SOME_GROUP,DC=COMPANY,DC=COM":"group1"
activeDirectoryRealm.authorizationCachingEnabled = false
ldapRealm = org.apache.zeppelin.server.LdapGroupRealm
# search base for ldap groups (only relevant for LdapGroupRealm):
ldapRealm.contextFactory.environment[ldap.searchBase] = dc=COMPANY,dc=COM
ldapRealm.contextFactory.url = ldap://ldap.test.com:389
ldapRealm.userDnTemplate = uid={0},ou=Users,dc=COMPANY,dc=COM
ldapRealm.contextFactory.authenticationMechanism = SIMPLE
also define roles/groups that you want to have in system, like below;
[roles]
admin = *
hr = *
finance = *
group1 = *
All of above configurations are defined in the conf/shiro.ini file.
NOTE : This documentation is originally from SECURITY-README.md.
